
If your company works anywhere within a Department of Defense supply chain (or hopes to), the new CMMC cybersecurity standard will soon be part of your life. Are you confused by the alphabet soup and uncertain about what it all means?
Here’s what you need to know:
What is this new standard?
It began in 2010, when the federal government defined Controlled Unclassified Information (CUI). This provided a unified standard for labeling and handling sensitive government information such as health documents, engineering plans or legal documents. Since 2018, the DoD has required its contractors to comply with NIST 800-171 as a control for properly handling CUI. (NIST 800-171 was published as a Defense Federal Acquisition Regulation Supplement, or DFARS.)
The government allowed organizations to self-certify their compliance with NIST 800-171, leaving some obvious gaps. The remedy is the Cybersecurity Maturity Model Certification (CMMC) program, which is scheduled to start appearing in DoD Requests for Proposal (RFPs) this fall. The Pentagon has stated that all DoD contracts will contain CMMC requirements by 2026.
How many certification levels does CMMC have, and which one do I have to meet?
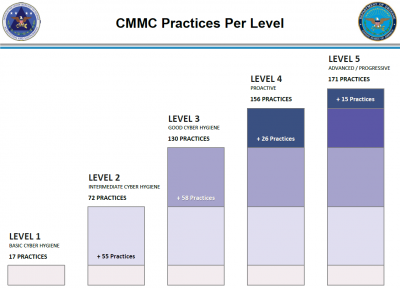 The standard has five levels, all of which include standards for both digital and physical security. All DoD contractors will be required to achieve at least Level 1. This “basic cyber hygiene” level includes familiar steps such as installing and regularly updating antivirus software.
The standard has five levels, all of which include standards for both digital and physical security. All DoD contractors will be required to achieve at least Level 1. This “basic cyber hygiene” level includes familiar steps such as installing and regularly updating antivirus software.
Any contractors with access to CUI will be required to achieve at least Level 3, which is a big step up from Level 1’s 17 controls to Level 3’s 100+ controls.
All DoD RFPs and Requests for Information (RFIs) will specify the required CMMC level. A company’s CMMC certification will last for three years.
Do all of a company’s physical locations require certification?
Any site that handles sensitive information must be certified. A third-party consultant can help you determine whether various sites in your organization require accreditation.
Do my subcontractors need to be certified?
In general, yes. At a press conference announcing CMMC, Ellen M. Lord, under secretary of defense for acquisition and sustainment, stated that, from a hacker’s perspective, “Attacking a sub-tier supplier is far more appealing than a prime [supplier].” Lord did clarify, however, that the required level may be different for a prime contractor and its subs.
The exception is a vendor who sells you raw materials such as steel or wire. Because those vendors have no access to sensitive information such as engineering plans, they do not need certification.
Who actually performs the accreditation?
Companies could perform self-certification under NIST 800-171, but CMMC won’t allow that. The CMMC Accreditation Body will be accrediting Certified Third-Party Assessment Organizations (known as C3PAOs) and registered assistance providers (known as RPOs) to certify companies and assist them with updating their controls to meet various levels of CMMC. CMMC-AB has started accepting applications and is in the process of certifying C3PAOs and RPOs so they can provide the necessary support to current and aspiring federal contractors.
How much time do I have to comply with this standard?
You can bid on a new contract before receiving your certification, but you must be accredited by the time the contract is awarded. Based on Pratum’s experience with previous government standard rollouts, we expect the DoD may provide a “waterfall” approach that gives vendors a series of required milestones for some lower risk contracts. The DoD will be motivated to work with current vendors to help them achieve this standard and continue with existing relationships.
How should my company approach this process?
The most effective approach is to get help preparing for the accreditation process to ensure you pass. Depending on your current cybersecurity program maturity, plan on a minimum of six months to evaluate your current posture, prepare for the audit and complete the audit. Here’s a suggested roadmap:
- Hire a third-party security firm to help evaluate your organization’s current posture compared to the level you need to achieve. Look for a firm with experience in complying with past government standards. Note that one vendor cannot serve as both your consultant in preparing for the audit and the auditing organization.
- Use the assessment to address any shortcomings before your audit.
- Retain a C3PAO to perform the audit.
- Correct any weaknesses revealed during accreditation. You may be required to create a Plan of Action and Milestones (POAM) to track and report on remediation of problem areas in order to keep a contract.
A local PTAC/MEP agency such as CIRAS also would be happy to help you get started.
To learn more, visit the Defense Department’s official CMMC page or contact CIRAS project manager Shankar Srinivasan at srigshan@iastate.edu.
You also can visit Pratum’s CMMC page at www.pratum.com/cmmc.