We are often asked to help a company understand what their contract compliance requirements are regarding cybersecurity in federal contracting. One way to understand those requirements is to look at your contract or solicitation and identify what cyber clauses are included. Below is a quick guide to identifying those clauses and understanding what obligations they impose. For further reading, check out this info pulled together by our friends at the Wisconsin APEX Accelerator.
FAR Clause
This clause may apply if you are doing business with any federal agency.
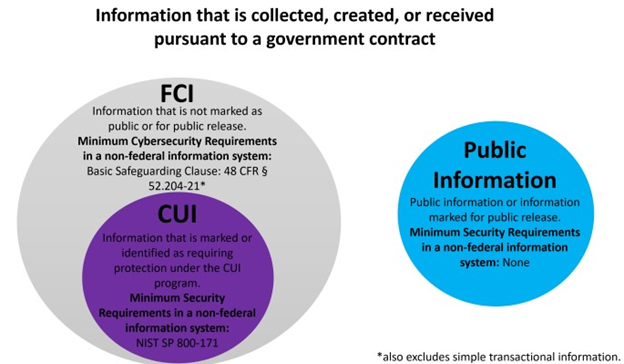
- FAR 52.204-21 Basic Safeguarding of Covered Contractor Information Systems – This clause requires you to comply with 15 basic security requirements to protect a category of information classified as Federal Contract Information (FCI). There are no requirements or additional steps required to ensure compliance with these 15 requirements. When a company accepts a contract with this clause, compliance is expected. This clause must also be flowed down to all subcontractors, including those for commercial items, as a subcontractor may have FCI residing in or transiting through its information systems.
DFARS Clauses
These clauses apply only to contracts with Department of Defense (DoD) agencies. The two asterisked clauses are solicitation provisions only that obligate you to comply with the other two contract clauses.
- DFARS 252.204-7008* – Compliance with Safeguarding Covered Defense Information – This clause is found in solicitations (not contracts) and states that by submitting an offer to this solicitation, you represent that you will implement the NIST SP 800-171 requirements. This clause specifies compliance with the DFARS 252.204.7012 contract clause.
- DFARS 252.204.7012 Safeguarding Covered Defense Information and Cyber Incident Reporting – This contract clause requires compliance with NIST SP 800-171 and is meant to protect a category of information classified as Controlled Unclassified Information (CUI), which is different than FCI referred to above (See below diagram). NIST SP 800-171 requires you to meet 110 security controls and have a System Security Plan (SSP) and a Plan of Action and Milestones (POAM) for all controls that you don’t yet have in place.Additional requirements are also addressed regarding cloud computing, cyber incident reporting, malicious software, media preservation and protection, and flow down requirements to name a few.
- DFARS 252.204-7019* – Notice of NIST SP 800-171 DoD Assessment Requirements – This clause is found in solicitations (not contracts) and states that “in order to be considered for award” the offeror is required to complete a NIST SP 800-171 DoD Self-Assessment and upload their score to the Supplier Performance Risk System (SPRS). This clause specifies compliance with the DFARS 252.204.7020 contract clause.
- DFARS 252.204.7020 – NIST SP 800-171 Assessment Requirements – This clause requires each business to conduct an assessment of their Covered Contractor Information Systems (defined in DFARS 252.204-7012) required to comply with NIST SP 800-171, by using the DoD Assessment Methodology. It requires each business to review the status of each of the 110 security requirements using its System Security Plan and determine whether the requirement has been implemented or not implemented. A score of 110 will reflect full implementation of all the requirements. If a requirement is not fully implemented, points are subtracted from this score.
Once the assessment is complete, the business must upload the following information into the Supplier Performance Risk System (SPRS):
- Company CAGE Code
- Date the Assessment was Performed
- Assessment Standard
- Scope
- Total Summary Score
- Date a Score of 110 will be Achieved
This clause does not specify a minimum score required to be awarded a contract. These requirements will be in place until the Cybersecurity Maturity Model Certification (CMMC) program is fully implemented and operational. Currently, the expected date for the transition from using the basic assessment to CMMC is October 1, 2025.
To help our clients with cybersecurity requirements, CIRAS is bringing in an expert to discuss for two separate webinars, and we hope you can join us and bring your questions! The first, Cybersecurity Basics: Federal Contractor’s Roadmap to DFARS and FAR Compliance is on July 19, and the second, Cybersecurity Uncovered: A Defense Contractors Guide to NIST SP 800-171 is on July 25.
For more information, reach out to your CIRAS Government Contracting Specialist or fill out our Request for Counseling form!